CVE
CVE plugin overview
Rudder CVE plugin allows assessing security vulnerabilities in packages installed on managed nodes.
After installation, a new menu entry called "Vulnerabilities" in the "Security Management" section gives access to the main plugin interface.
It provides several views, by nodes or by CVE.
The view by nodes provides, for each node, a summary of identified vulnerabilities:
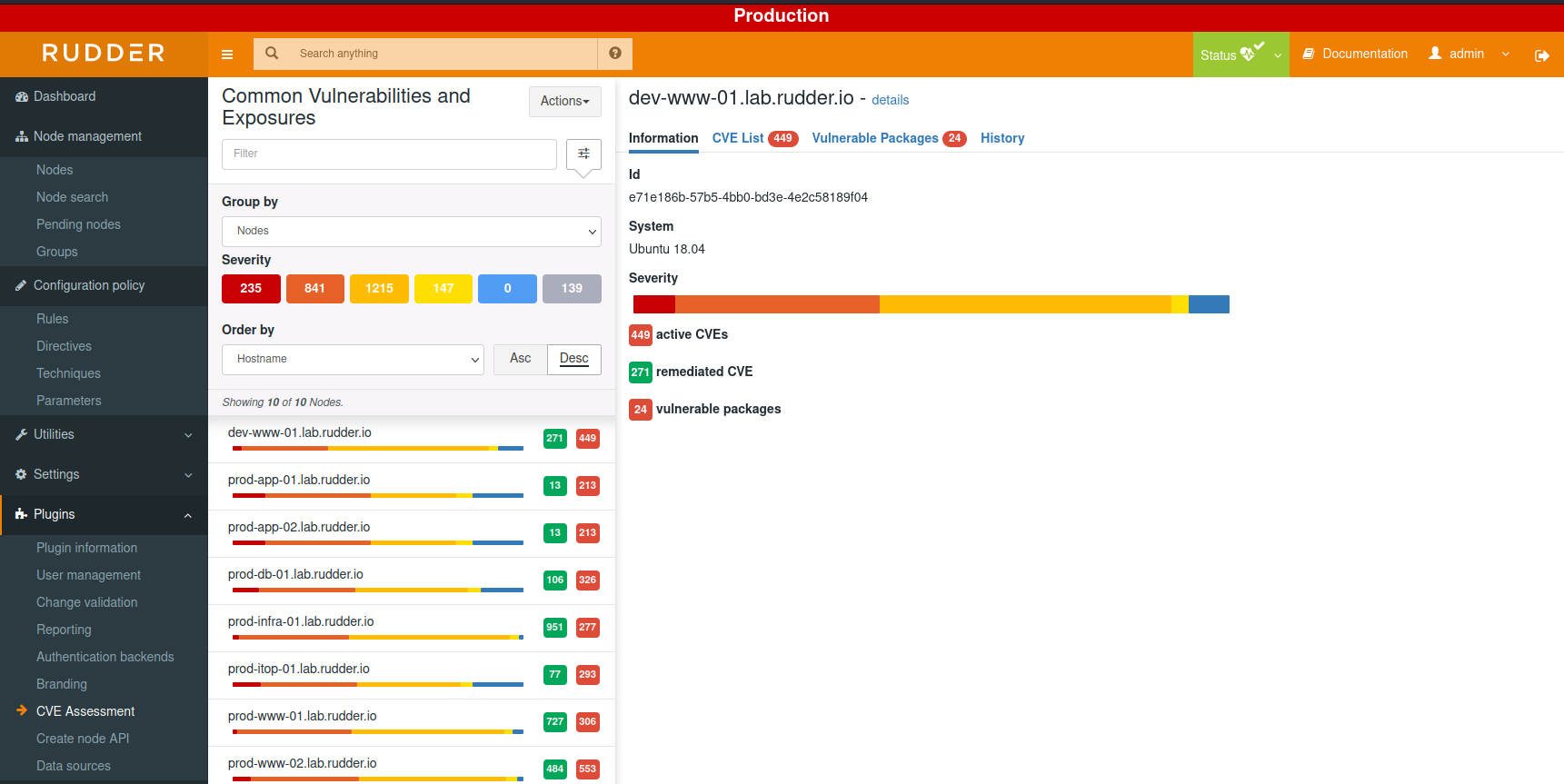
And a list of CVE and impacted packages:
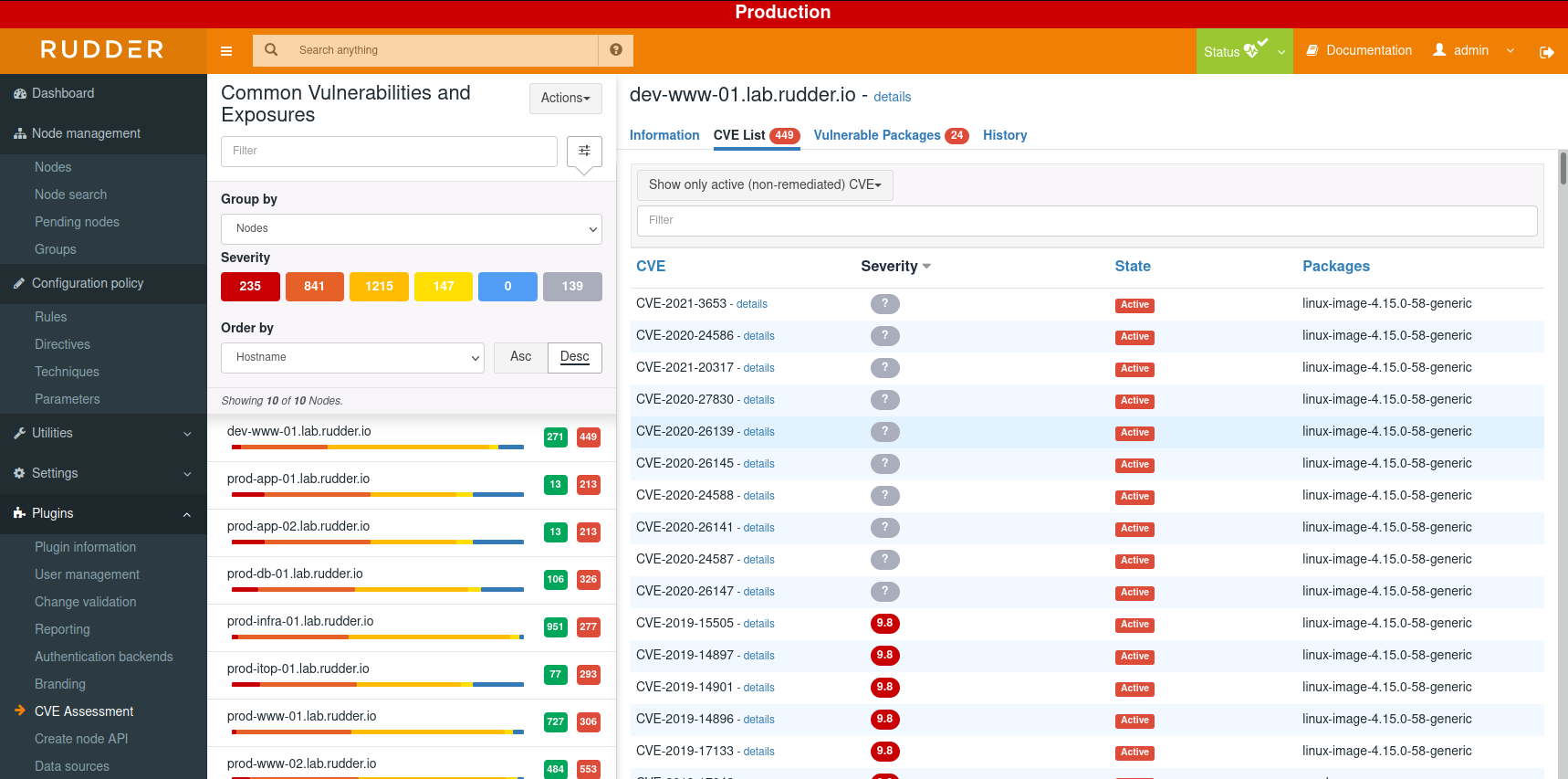
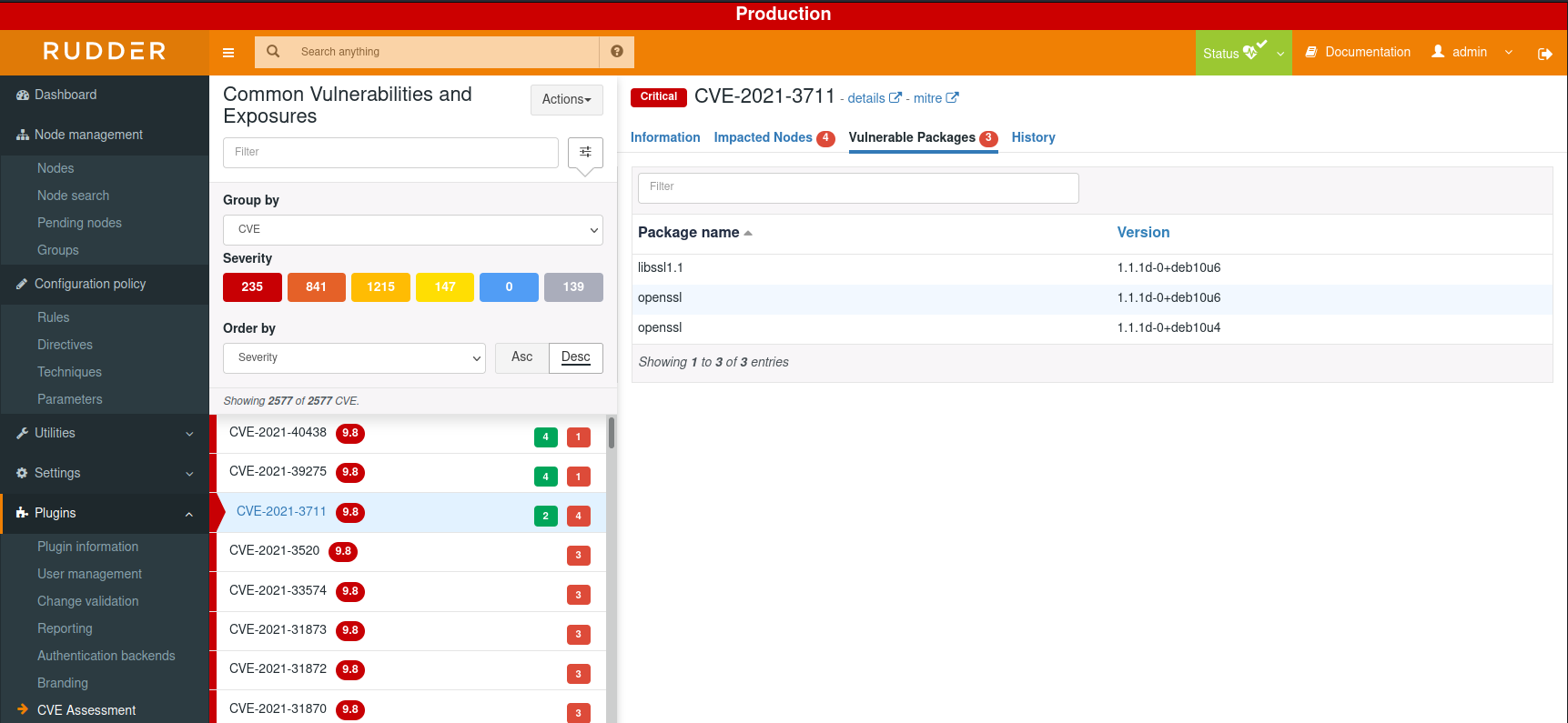
The view by CVE provides information about the CVE and status by node:
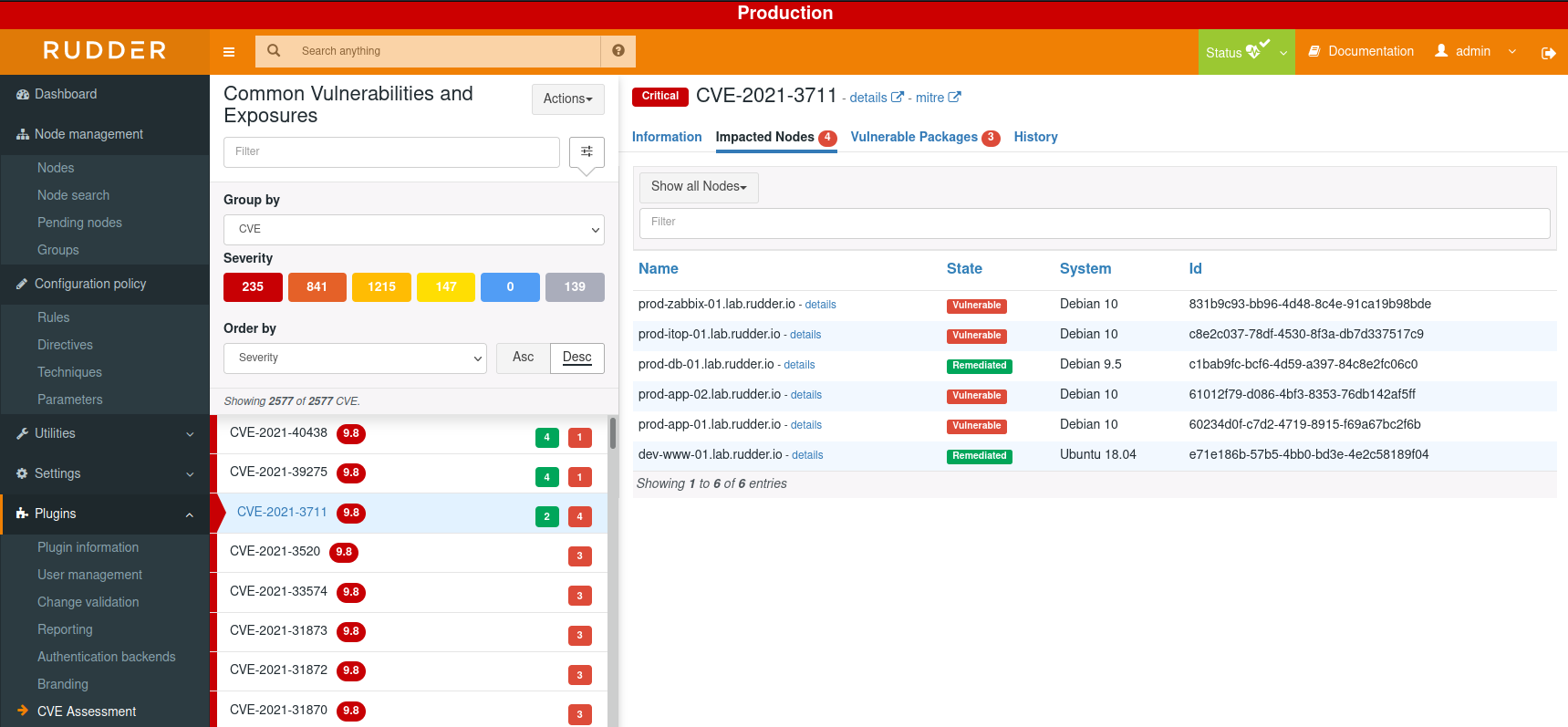
There are several filter options that you can explore and most importantly see in details each CVE.
CVEs' severity are classified descendant from critical, high, medium, low, info to unknown, each CVE identify vulnerable packages installed on a particular node and also has a given score and description.
There are actually 3 axes that impact identifying and classifying vulnerabilities: The CVEs archives used to do so depending on which year, The OS installed on the nodes and the packages that are installed on the nodes.
As we said above, you can click on each CVE and read more information about which nodes are impacted and packages too, in addition, you can search elsewhere about a specific CVE using its unique identifier.
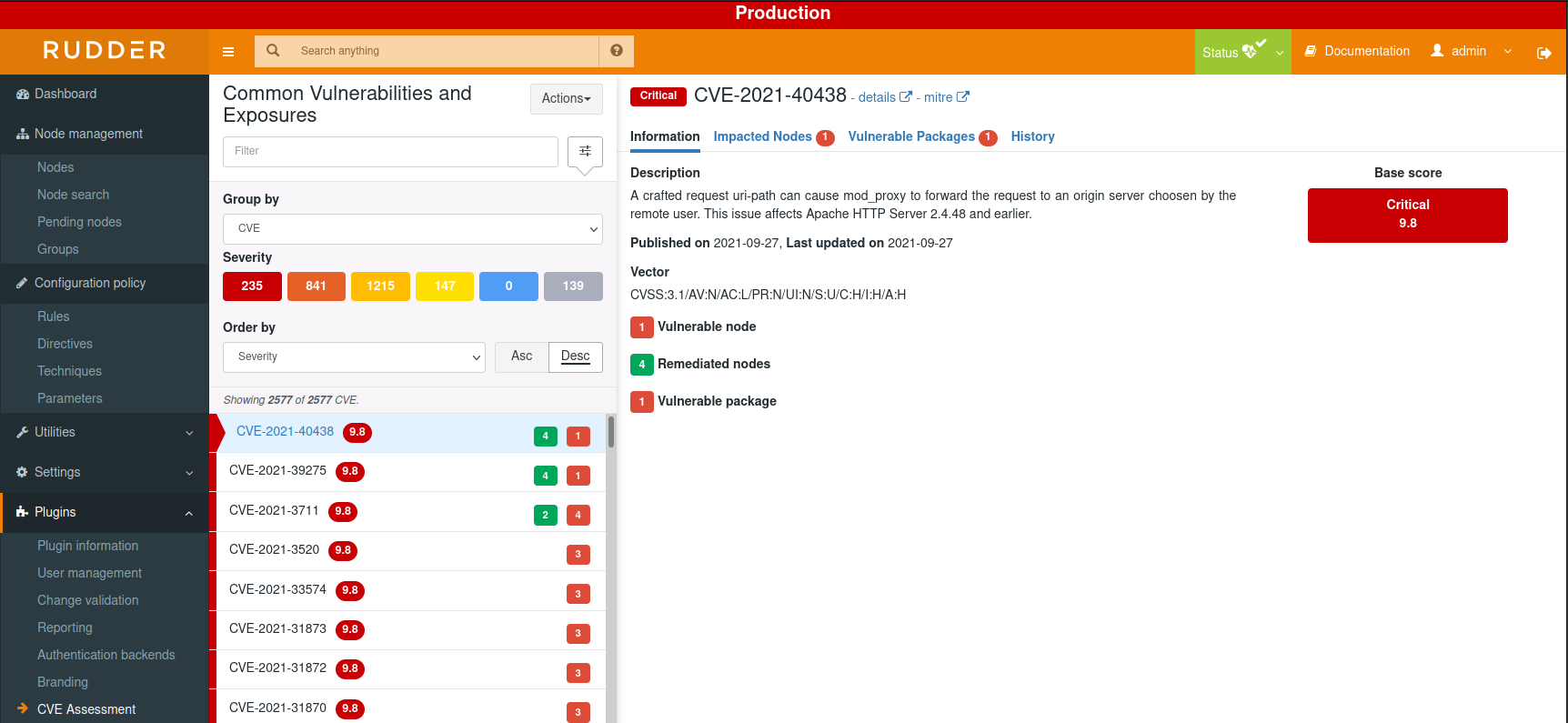
You can also switch the view to have a "By Node" view that allows you to check which CVE were detected for each node and see all vulnerable packages installed on this node.
Installation, requirements and settings
| This plugin uses an internet services provided by Rudder to work. |
Your Rudder root server needs access by HTTPS to URL https://api.rudder.io/cve/*
Compatible OSes
CVE plugin is compatible with the following systems:
-
Debian 8 to 12
-
RHEL 5 to 9 (and derivatives)
-
SLES 11 to 15
-
Ubuntu 14.04 to 24.04
-
Amazon Linux
-
Oracle Linux 5 to 7
-
Windows (any versions supported by Rudder)
And in general, any version of previous systems that is still actively maintained by their vendor is compatible with our CVE plugin ( OVAL source available and/or active security tracker for this version)
Proxy configuration
If your Rudder Server can access internet only through a proxy, you should define how to access your proxy in the configuration file of the rudder package command (/opt/rudder/etc/rudder-pkg/rudder-pkg.conf). You will have to add the proxy parameters (proxy_url, proxy_user, proxy_password), resulting in a file as follows:
[Rudder]
url = https://download.rudder.io/plugins
username = <your_plugin_download_username>
password = <your_plugin_download_password>
proxy_url = <your_proxy_address:port>
proxy_user = <your_optionnal_proxy_username>
proxy_password = <your_optionnal_proxy_password>JVM memory sizing
The CVE plugin may require additional memory for its operation, at least 4GB.
If you see out of memory errors in the logs or the plugins fails to update CVE information,
make sure the server system has enough available memory and increase the webapp memory limit in /etc/default/rudder-jetty:
# 2048MB is the low limit with the CVE plugin
# consider adding 2GB to previous value to make sure things run smoothly
JAVA_XMX=4096Then restart the server with systemctl restart rudder-jetty.
Permissions provided for custom-roles
The CVE plugin comes with its own atomic permissions that you can be used with custom roles from the user management configuration in Rudder.
These permissions are:
-
cve_read: that permission allows a user to access to vulnerability assessment and get information regarding when check were done, -
cve_write: that permission allows to start the interactive actions like start new check, update CVE base, etc.
Vulnerability assessment
A note about CVE
CVE system is a catalog or more like a database that contains all known vulnerabilities and exposures that can be identified in organizations' information systems.
Each vulnerability has its own unique identifier under the form of CVE-AAAA-NNNN (AAAA is the year of publication and NNNN is an id number) and
also presented by a brief description and other various information related to it.
This database can be used by organizations in different ways such as integrating and linking it with other tools (Which what CVE Plugin in Rudder offers), so they can be aware of security threats in their information systems and consequently improve them.
Plugin operation
Rudder use a package-based check for the discovery of vulnerabilities.
To find out which vulnerabilities affect your nodes, Rudder analyzes the list of all packages of a system and checks whether they are vulnerable or not by using a remote Rudder service. This service bases its analysis on Linux distribution channels of vulnerabilities information.
Outgoing data
Data sent to the Rudder CVE services are JSON payloads with only OS and package related information. There is no node-specific information (like hostnames, IPs, etc.) going out of the Rudder root server.
All package information are aggregated on all nodes to avoid knowing what nodes have what packages.
Exact information sent is:
-
OS related information (family (
debian, etc.), version (10), kernel version) -
and a list of pair of (package name, package version).
Our API then answers with the list of vulnerabilities for each package, and Rudder root server locally does the processing to match-back nodes and their vulnerabilities.
Interactive check and CVE database update
The plugin has two sections that can be consulted via the "Actions" buttons to interactively update the CVE assessment or to make a CVE check on your nodes.
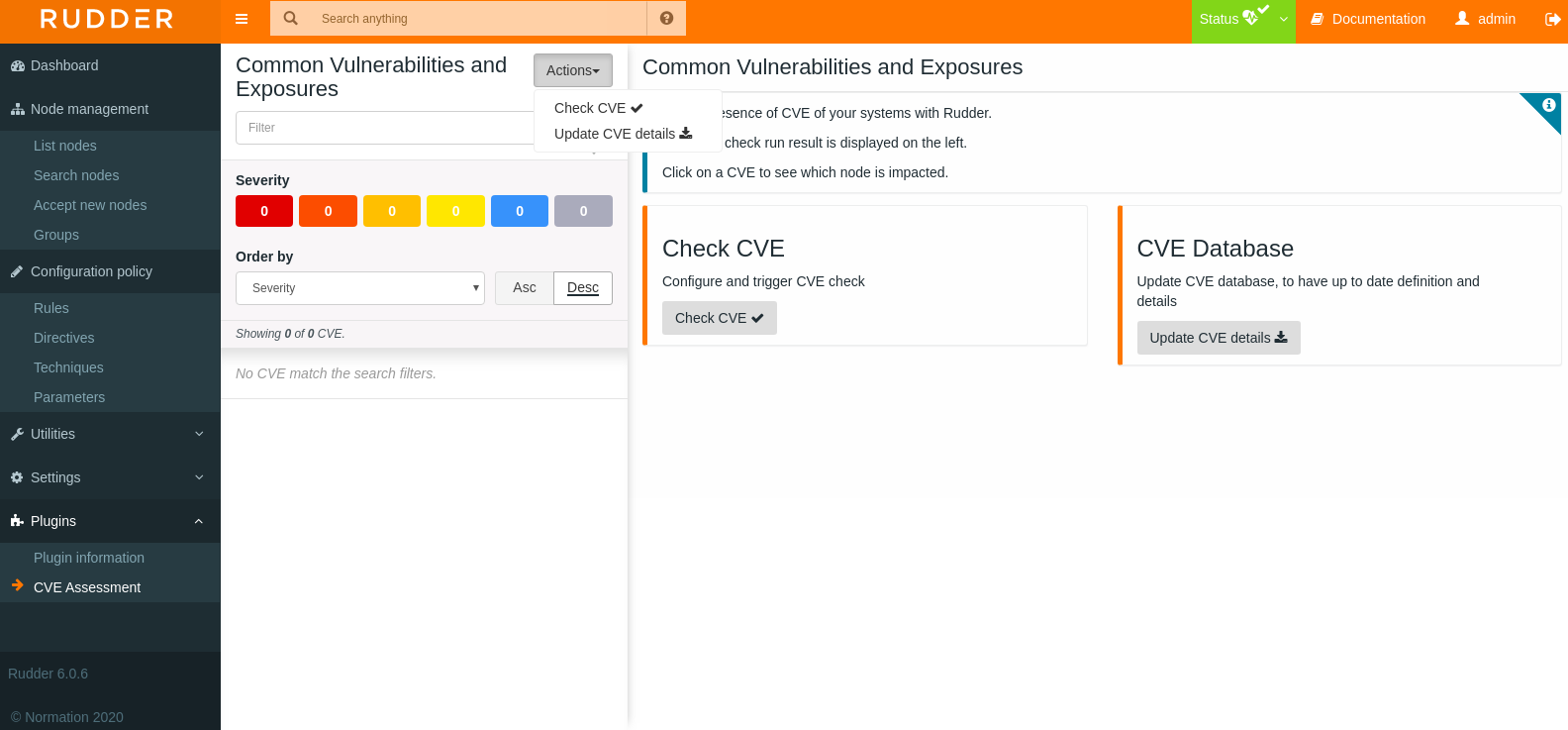
-
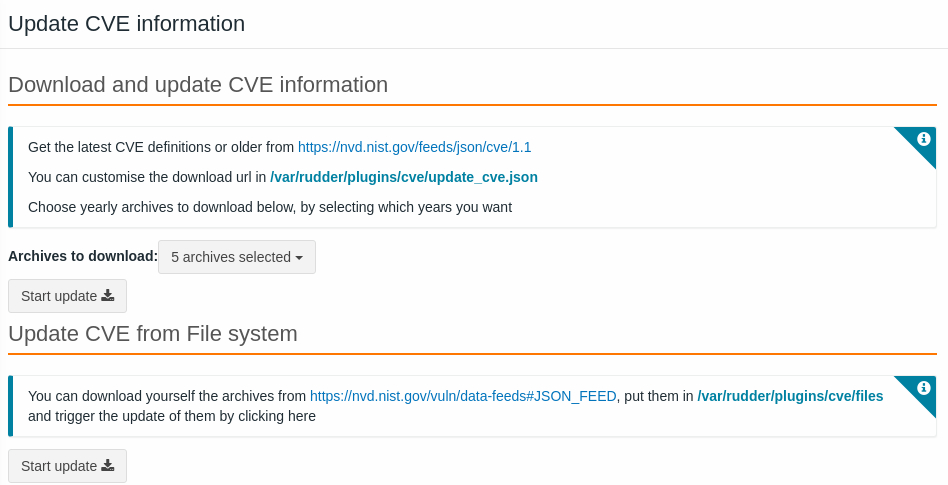
Updating the CVE details means you load the CVE base, that are under
/var/rudder/plugins/cve/files/directory, by simply choosing which year(s) of the archives to download, you can also as specified, customize the download url in the Json configuration file on your system/var/rudder/plugins/cve/update_cve.json
Fetching CVE details can be a long task as there is a lot of data to process. The request can time out, but Rudder will continue to get the data from the database, so don’t worry about it
Note than you can also load the CVE base manually by putting the Json archives under the /var/rudder/plugins/files/ directory.
-
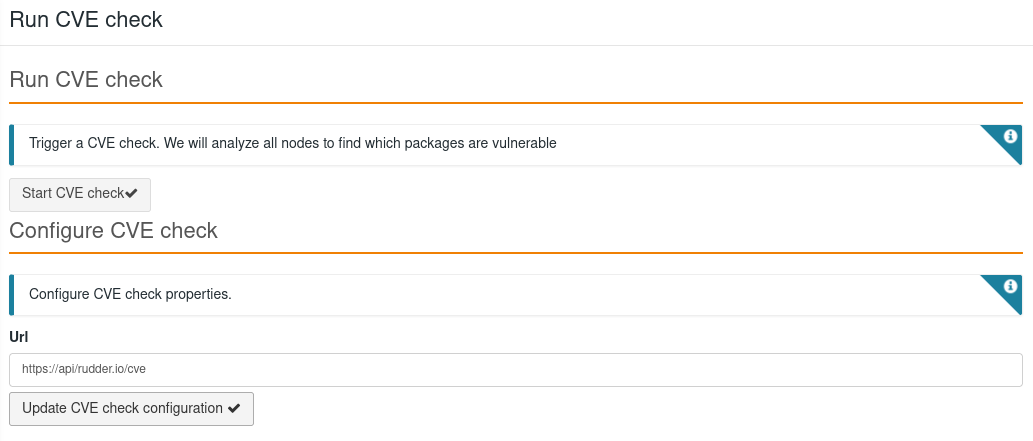
After initializing the database with the appropriate archives, you can perform the CVE check on all your Rudder nodes by running the check in the
Check CVEmenu
CVE analysis can take a while depending on the number of your nodes and the packages installed on them. And an error can occur due to request timeout, refresh the page, and you will have your result available.
CVE analysis is also done every day, so you don’t have to click on the button each time you need it.
How CVE are detected.
On Unix systems, CVE are detected through packages installed on each node (based on software from the inventory). We check within OVAL and security trackers maintained by each Vendor whether the version of the package is vulnerable to a CVE or not.
On Windows systems, CVE are detected by checking which KB (Windows updates) are not yet installed on each (through Software updates in Inventory). We check in Microsoft security databases, which CVE are fixed by non installed KB, and we report that your system is vulnerable to this CVE
In both cases, we only report CVE that can be fixed, either by upgrading your package to latest version or installing Windows updates.
Vulnerabilities score
We define a score for vulnerabilities based on how many CVE were found and their vulnerabilities
-
A: There is no critical CVE (score > 9.0) and there is less than 50 CVE found
-
B: There is between 1 and 5 critical CVE or between 50 and 75 CVE found
-
C: There is between 5 and 20 critical CVE or between 75 and 125 CVE found
-
D: There is between 20 and 50 critical CVE or between 125 and 175 CVE found
-
E: There is between 50 and 80 critical CVE or between 175 and 250 CVE found
-
F: There is more than 80 critical CVE or more than 250 CVE found
How can I remediate my security vulnerabilities?
You can remediate security vulnerabilities by upgrading your systems, and Rudder provides you different way to achieve this. It can be achieved through classic directives or to have a better control over your upgrades you can use our system-updates plugin in which you can create and schedule patch management campaigns.
But you need to target specific nodes, because you may not want to update all your nodes but only those that are vulnerable, and that’s where CVE plugin comes to your help. The CVE plugins allows you to create dynamic groups based on whether nodes are vulnerable to a CVE or not. The group is using a property on nodes that is managed by CVE plugin, and it adds or removes the property after a CVE check (depending on the CVE presence). Once the group is created you can use it in your own directives and update campaign to remediate your nodes.
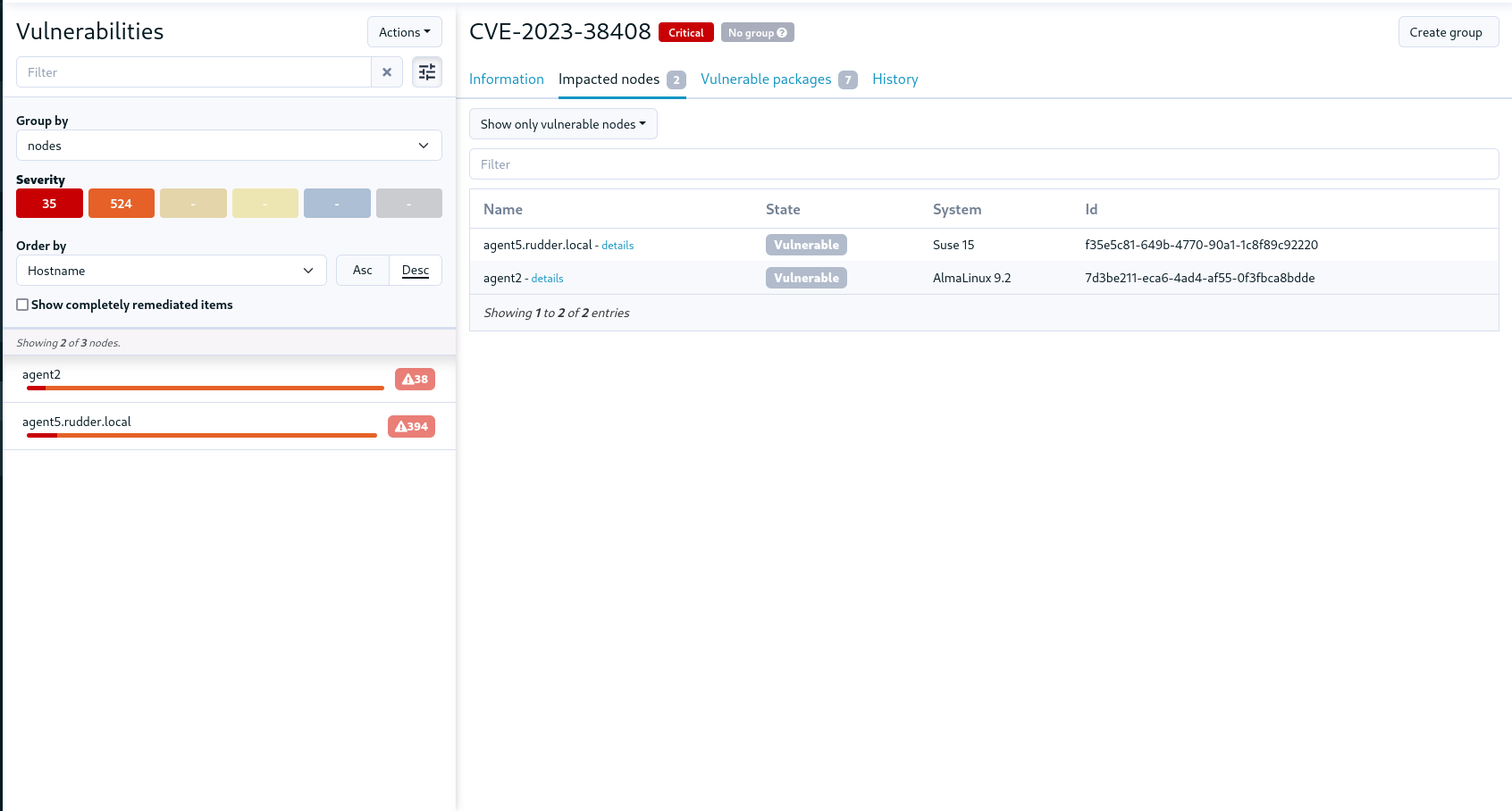
The group is created by clicking on a button in the top right corner of a CVE, and the group is created in a dedicated group category (CVE groups). After the group is created, you can delete it, the creation button is replaced by a deletion one.
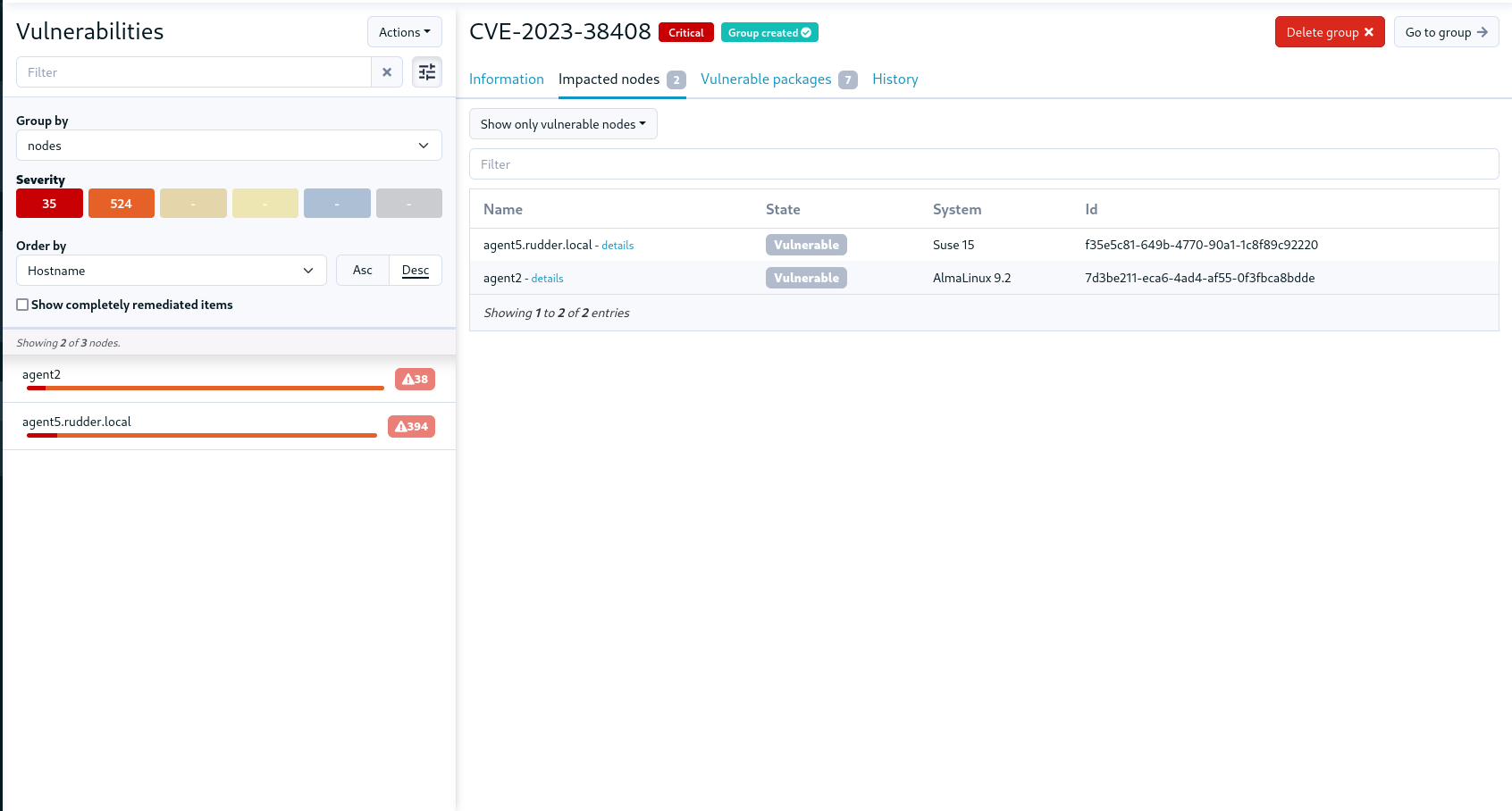
In the future, we expect to automate further with system-updates plugin to create remediation campaign directly from CVE page, if you are interested, don’t hesitate to come back to us.
← Consul Node properties data sources →