Rudder 8.2 release notes
We’re thrilled to announce the availability of Rudder 8.2. The 8.X versions are mainly dedicated to developing the compliance axis, and the 8.2 release is no exception.
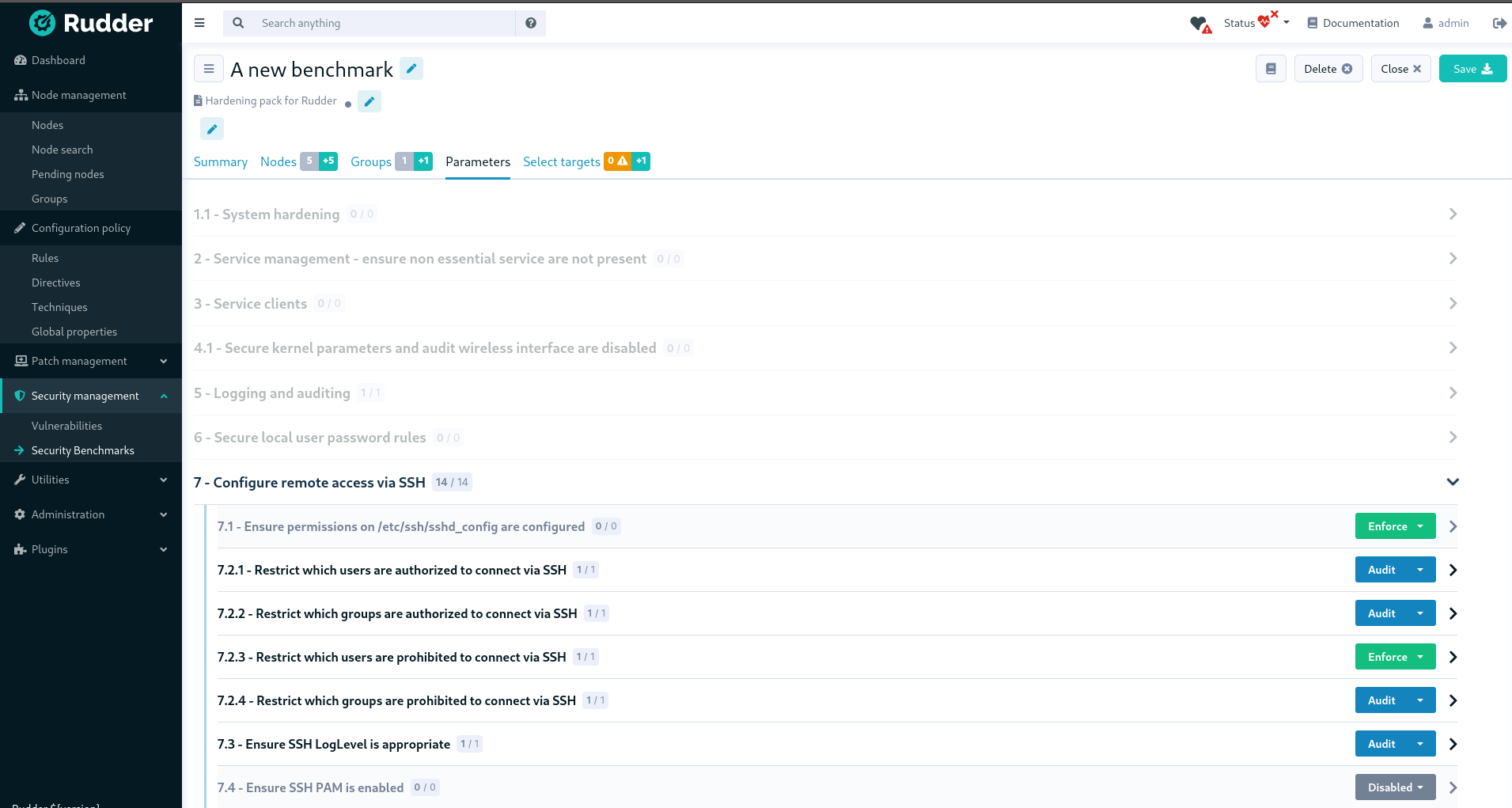
🛡️ Security benchmarks
Rudder already provided powerful tools to audit and apply security policies, possibly derived from standards like CIS, STIG, etc.
The most important need when applying these kinds of policies, if users want them to be actually usable and not just a theoretical exercise, is the ability to finely configure and tune them to match the reality of the systems: exceptions, different configurations, etc. This new feature provides a way to achieve this with minimal effort, by relying on the powerful data management capabilities of Rudder.
It also provides a dedicated sub-score, independent of general configuration policies, allowing for a clear overview of the security level of the systems.
🔼 Patch & vulnerability management
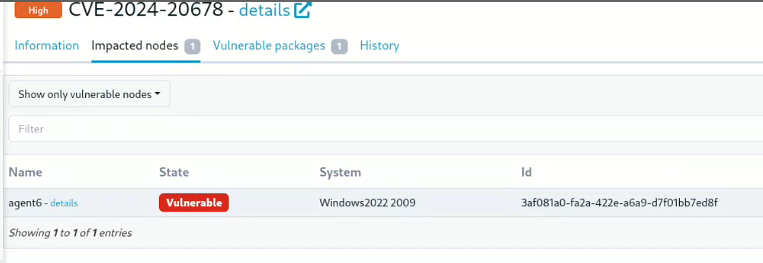
🪟 Manage Windows system vulnerabilities
The vulnerabilities tracking feature, which previously only supported Linux systems, is now also compatible with Windows. It allows tracking known vulnerabilities in the system, fixed by available KBs.
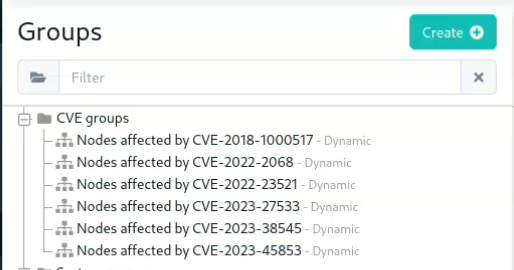
⚠️Create groups based on vulnerability presence
The new feature allows creating groups based on the presence of vulnerabilities, directly from the vulnerability entry in the interface. The groups can then be used in policies, reports, etc. This is useful to apply specific mitigation, plan a targeted upgrade campaign, etc.
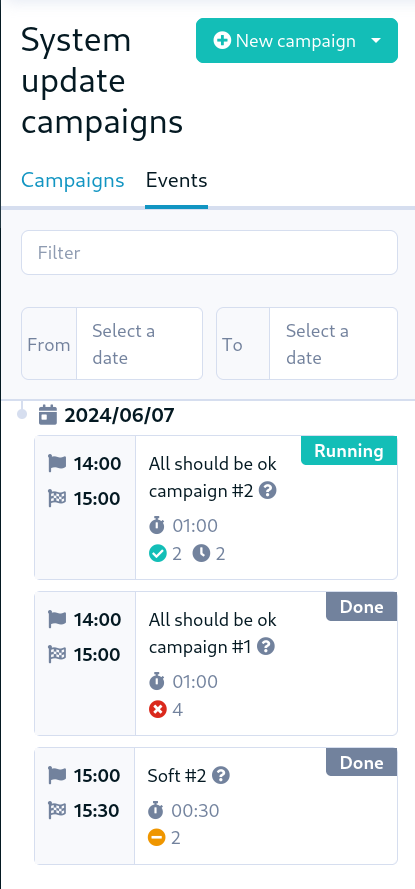
🩹 Patch management outcome display
The patch management campaign view now provides a clear outcome of the campaign, with a summary of the number of patches applied, failed, etc. directly in the campaign view.
🔒 Security-only system update (🐧 on Linux)
The patch campaigns for Linux gained the ability to apply only the security upgrades. It uses the matching package manager feature depending on the target distribution. This feature requires the agent in version 8.2
Users now have three options: full system upgrade, security system upgrade, or target upgrade from a list of packages.
📊 Manage workstations and embedded systems with compliance persistence
Rudder is built around continuous feedback from the agents to the server. This allows displaying real-time data. But this behavior does not fit some use cases when machines are unable to communicate with the server continuously for different reasons: desktop/laptops, which are shut during the night, embedded systems with inconsistent connectivity, etc. Currently, they will appear as unavailable "gray nodes", and lower the global compliance.
For these cases, it will now be possible to keep the latest received data and use them within reporting, for a configurable time.
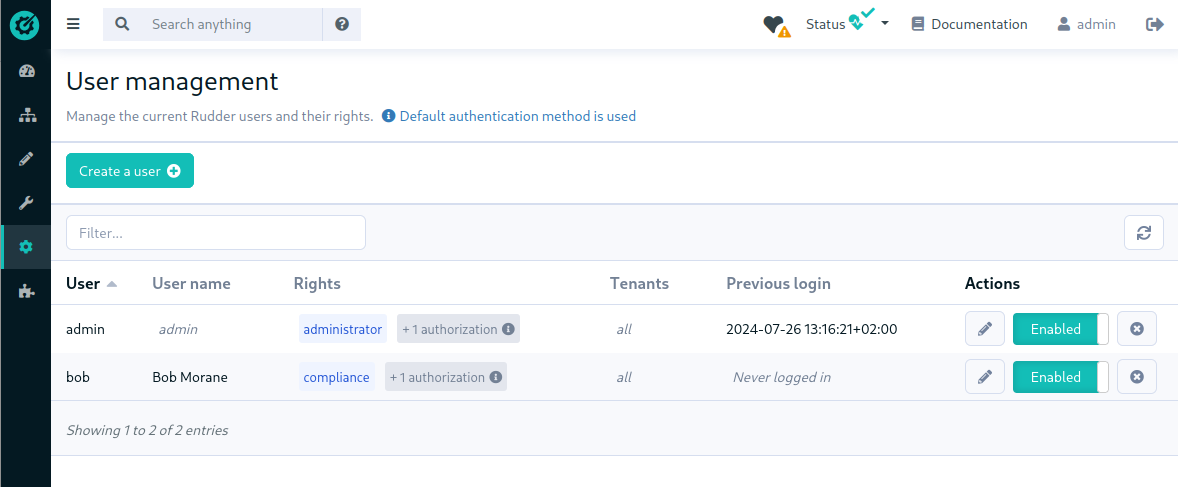
👥 The user management interface is now a core feature
The interface for user management previously provided as part of a plugin is now part of the main application. It was also notably enhanced with a new list view matching other pages' style.
Under the hood
Local account hashes are now configurable per user
This will allow users still having deprecated hashes to gradually migrate to bcrypt, the modern password hash available in Rudder.
⚙️Introducing the node modules
We introduce modules to extend the agent, with two focus: logging and reliability. These modules are written in Rust, and the first implementation is for system updates, to communicate with package manager.
📜 New Windows variable evaluation context
We are changing the variable evaluation for the Windows agent, switching to a Rudder-specific syntax (like for Linux). This new format prevents code injection in variables.
Continue frontend hardening with strict CSP headers
In the same vein as the previous releases, the frontend is now more secure thanks to the use of struct Content Security Policy headers in more pages.
💾 Installing, upgrading and testing
-
Install docs for Debian/Ubuntu, RHEL/CentOS and SLES
Main changelogs →