OpenSCAP
OpenSCAP is an ecosystem that provides several tools to assist administrators and auditors with assessment, measurement, and enforcement of security baselines. It allows the use of different profiles aligned with different standards such as PCI-DSS.
The plugin provides a Technique to execute the OpenSCAP tool at regular interval, centralize the generated report on the Rudder Server, and show the report in a new tab in the Node details for all Nodes having the OpenSCAP Technique.
Installation
-
Your Rudder server must have python-requests and rudder-api-client installed
-
Install the plugin on the Rudder Server with
rudder package
Usage
In order to use the Technique provided and get reports from your nodes, you will need to decline it in different directives following your requirements.
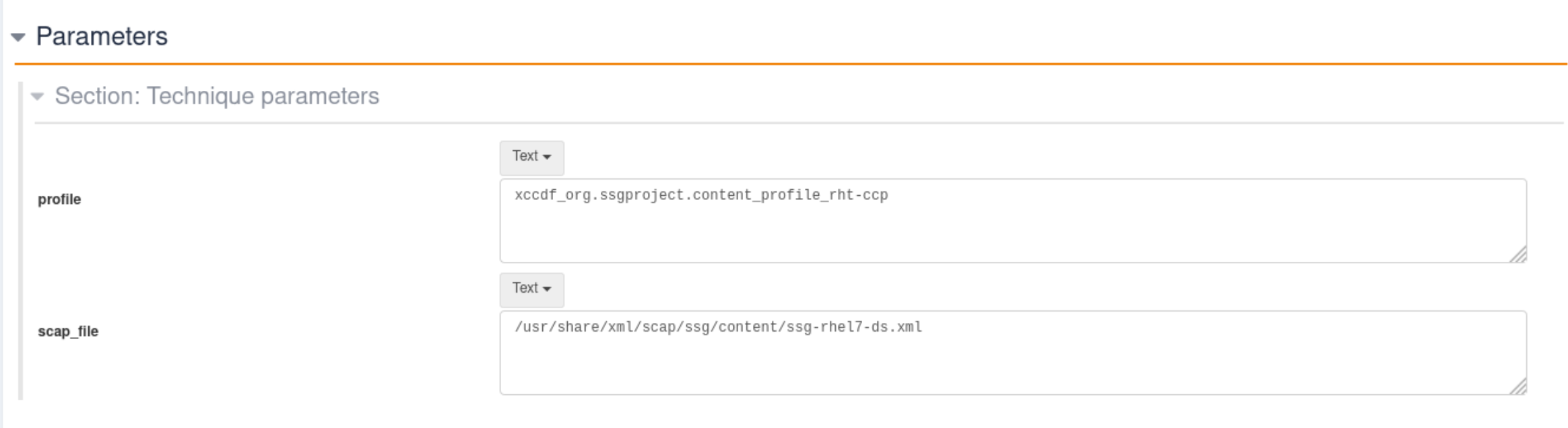
The technique comes with two parameters:
-
profilewhich is the profile name you want to audit -
scap_filewhich is the absolute path (on the node) of the SCAP content from which you will base the audit on
SCAP content refers to document in the XCCDF, OVAL and Source DataStream formats. These documents can be presented in different forms and by different organizations to meet their security automation and technical implementation needs. You can find more informations on the ComplianceAsCode GitHub project.
By default, available scap_files are located on /usr/share/xml/scap/ssg/content/ after installation of the openSCAP agent on the nodes. Given profiles for specific scap_files can be obtain with the command:
oscap info <scap_file>
The technique will take care of the openSCAP agent installation and will by default, trigger an audit every hour on your nodes. The reporting file will then be uploaded on your Rudder Server under the folder:
/var/rudder/shared-files/root/files/<node-id>/openscap_report.html
Usage on Ubuntu/Debian
OpenSCAP packages in Debian and Ubuntu repositories are very out of date, and it is necessary to get up to date profiles from OpenSCAP sources.
Example for Ubuntu 18.04 LTS:
# install openscap tools sudo apt-get install libopenscap8 python-openscap sudo apt install ssg-base ssg-debderived ssg-debian ssg-nondebian ssg-applications # install build dependencies for profiles apt-get install cmake make expat libopenscap8 libxml2-utils ninja-build python3-jinja2 python3-yaml xsltproc git clone https://github.com/ComplianceAsCode/content.git cd content # build up to date profiles ./build_product ubuntu18.04 # install the profiles to the system sudo cp build/*.xml /usr/share/openscap/
Then you can use the following parameters:
-
profile:
xccdf_org.ssgproject.content_profile_standard -
scap_file:
/usr/share/openscap/ssg-ubuntu1804-ds-1.2.xml
The reports are done every night, to trigger an immediate report add -D schedule_simple_openscap_repaired to your agent command like:
rudder agent run -D schedule_simple_openscap_repaired -ui
Rudder Webapp integration
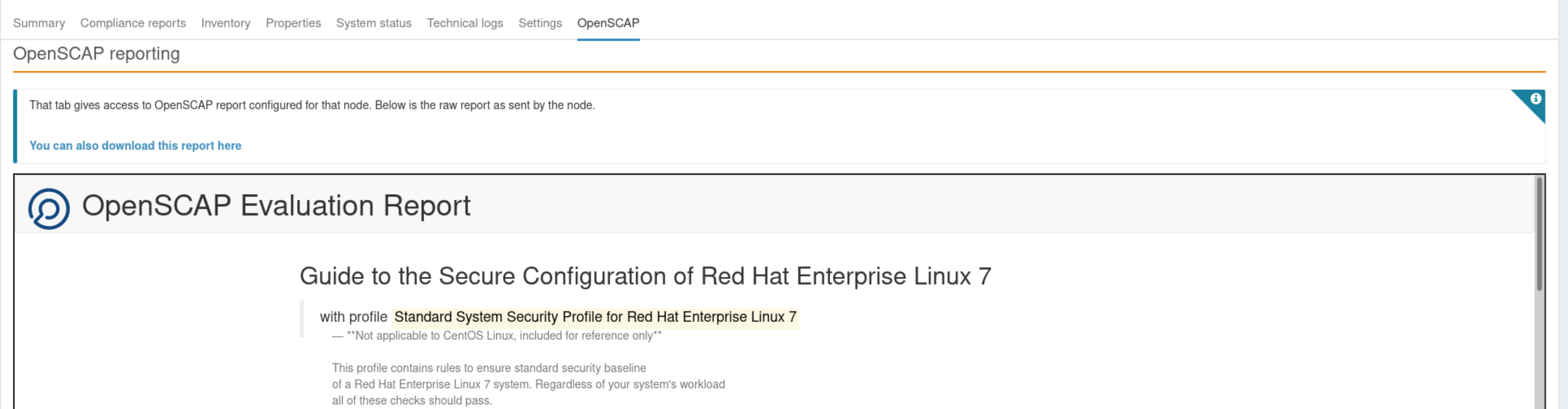
A new tab in Node Details called OpenSCAP is added by this plugin for nodes configured to have the OpenSCAP Technique running. It displays the report in an iframe in this tab, as it is sent by the node, without any sanitization yet.
A new API endpoint is also available:
-
/latest/openscap/report/{nodeId} : the OpenSCAP report
← Notification Reporting →