CVE
-
CVE system is a catalog or more like a database that contains all known vulnerabilities and exposures that can be identified in organizations' information systems. Each vulnerability has its own unique identifier under the form of
CVE-AAAA-NNNN(AAAA is the year of publication and NNNN is an id number) and also presented by a brief description and other various information related to it. -
This database can be used by organizations in different ways such as integrating and linking it with other tools (Which what CVE Plugin in Rudder offers) so they can be aware of security threats in their information systems and consequently improve them.
-
As part of the compliance and audit process in Rudder, actually do come the need of integrating it to manage and report information about vulnerable packages present on nodes.
-
To find out which vulnerabilities affects your Nodes, we analyse the list of all packages of a system and check whether they are vulnerable or not.
Setup
The CVE plugin may require additionnal memory for its operation, at least 4GB.
If you see out of memory errors in the logs or the plugins fails to update CVE information,
make sure the server system has enough available memory and increase the webapp memory limit in /etc/default/rudder-jetty:
# 2048MB is the low limit with the CVE plugin
# consider adding 2GB to previous vlaue to make sure things run smoothly
JAVA_XMX=4096Then restart the server with systemctl restart rudder-jetty.
Description
-
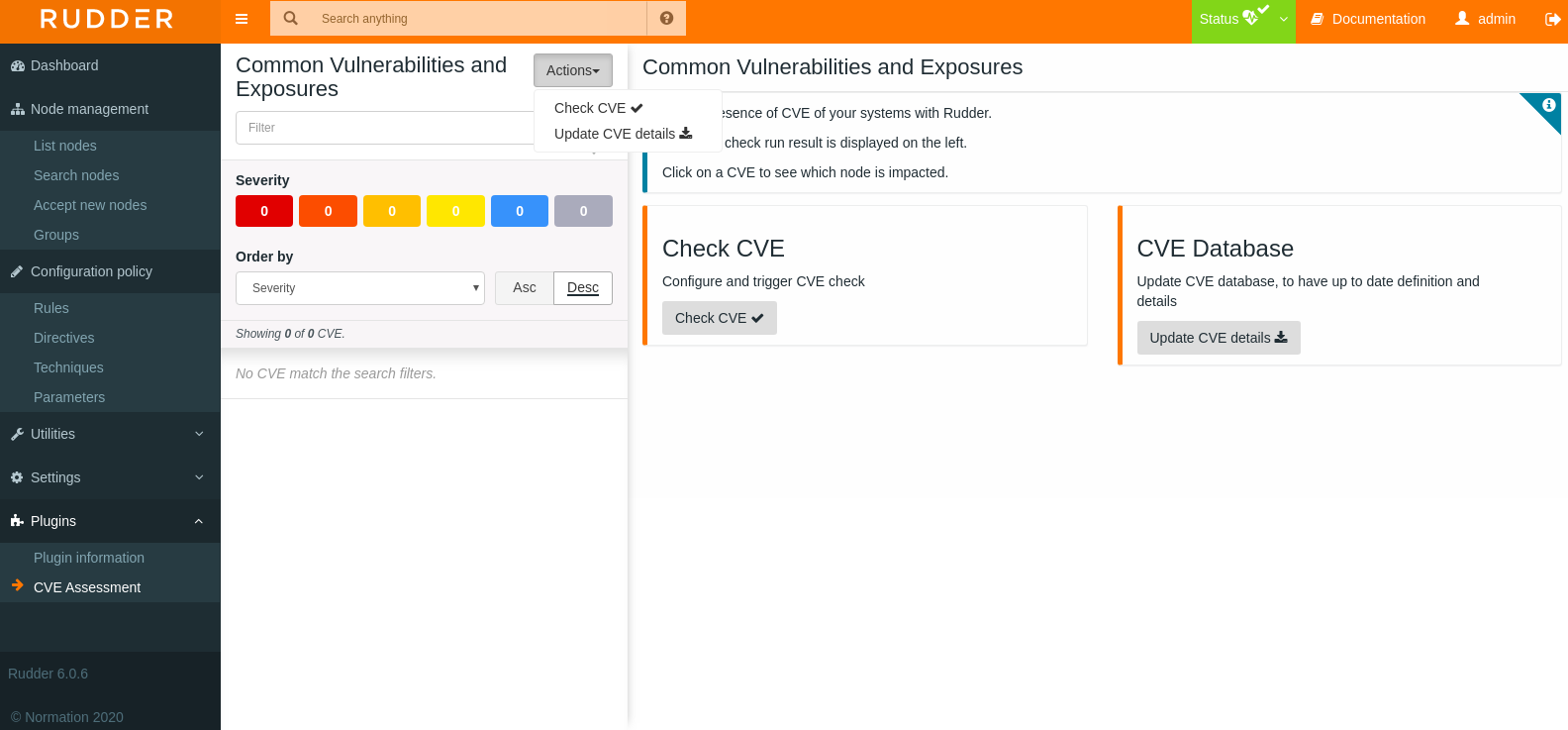
To explore and use the plugin, there is an entry that will be added after installation called “CVE assessment” in the “Plugins” section of Rudder menu which gives access to the main CVE management interface.
-
Below is a figure of the UI, it presents different keys and basic features, the most important one is that it allows you to visualize the list of CVEs that are present on the nodes.
-
There are several filter options that you can explore and most importantly see in details each CVE.
-
The plugin has two subinterfaces that can be consulted via the “Actions” button above, either you update the CVE details or you make a CVE check on your nodes.
-
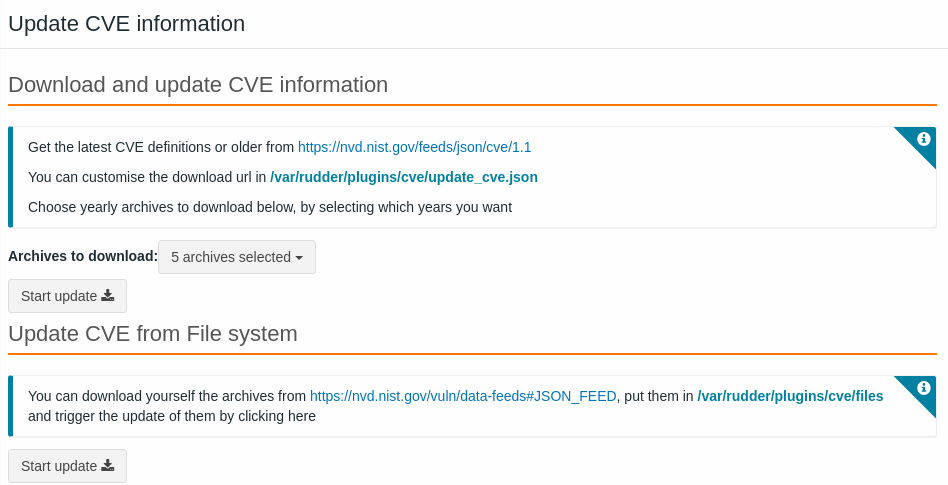
Updating the CVE details means you load the CVE base, that are under
/var/rudder/plugins/cve/files/directory, by simply choosing which year(s) of the archives to download, you can also as specified, customize the download url in the Json configuration file on your system/var/rudder/plugins/cve/update_cve.json
Fetching CVE details can be a long task as there is a lot of data to process. The request can timeout, but Rudder will continue to get the data from the database, so don’t worry about it
Note than you can also load the CVE base manually by putting the Json archives under the /var/rudder/plugins/files/ directory.
-
After initializing the database with the appropriate archives, you can perform the CVE check on all your Rudder nodes by running the check in the
Check CVEmenu
CVE analysis can take a while depending on the number of your nodes and the packages installed on them. And an error can occur due to resquest timeout, refresh the page and you will have your result available

-
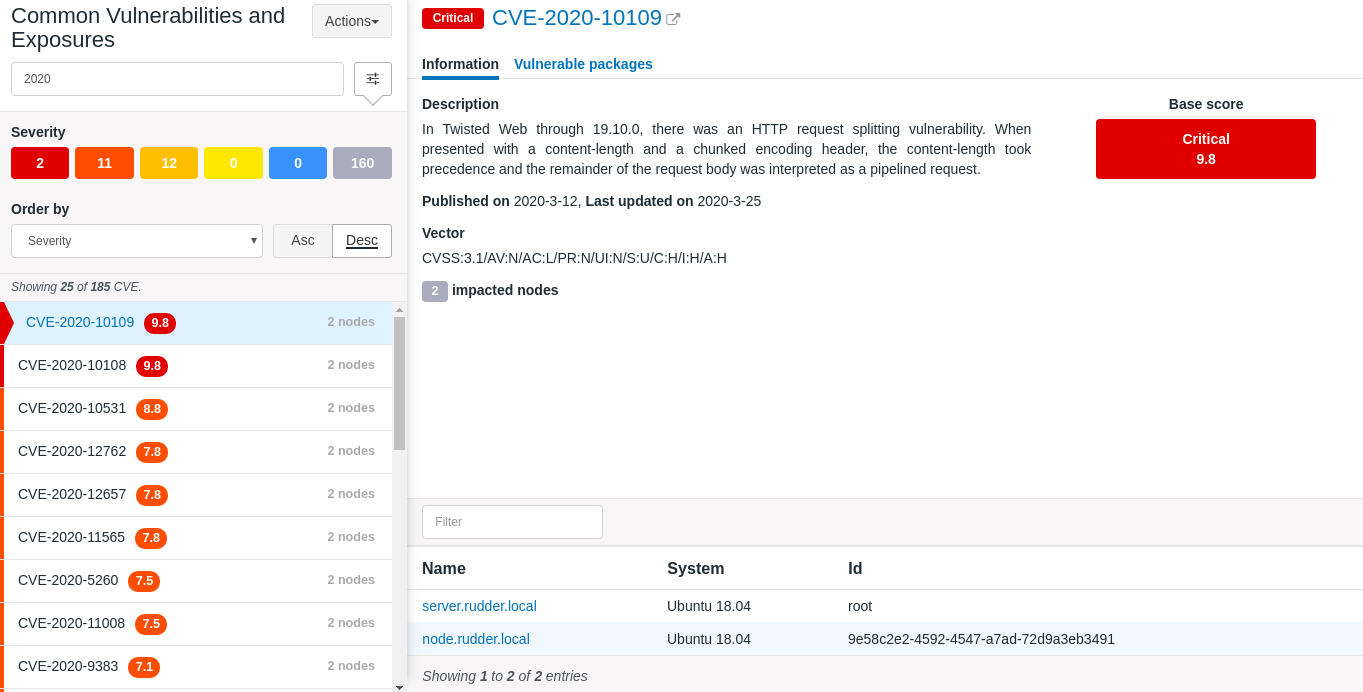
CVEs' severity are classified descendant from critical, high, medium, low, info to unknown, each CVE identify vulnerable packages installed on a particular node and also has a given score and description.
-
There are actually 3 axes that impact identifying and classifying vulnerabilities: The CVEs archives used to do so depending on which year, The OS installed on the nodes and the packages that are installed on the nodes.
-
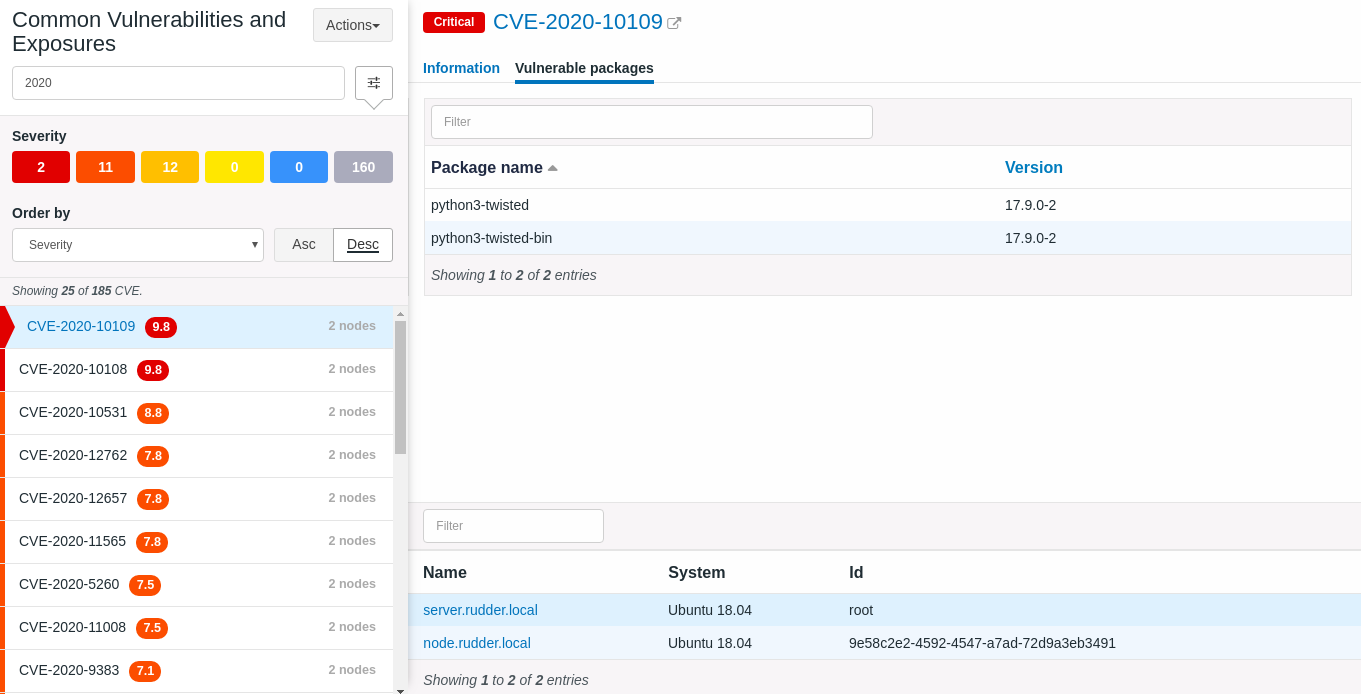
As we said above, you can click on each CVE and read more information about which nodes are impacted and packages too, in addition, you can search elsewhere about a specific CVE using its unique identifier.
-
You can also switch the view to have a "By Node" view that allows you to check which CVE were detected for each node and see all vulnerable packages installed on this Node.
Define proxy
If your Rudder Server can access internet only through a proxy, you should define how to access your proxy in configuration file of rudder package command (/opt/rudder/etc/rudder-pkg/rudder-pkg.conf). As of 6.1, You will have to add the proxy parameters (proxy_url, proxy_user, proxy_password), resulting in a file as follows:
[Rudder]
url = https://download.rudder.io/plugins
username = <your_plugin_download_username>
password = <your_plugin_download_password>
proxy_url = <your_proxy_address:port>
proxy_user = <your_optionnal_proxy_username>
proxy_password = <your_optionnal_proxy_password>← Create node Node properties data sources →