CIS
This plugin will bring a set of directives to help auditing the CIS benchmark with Rudder.
All directives will be provided in Audit mode enabled to prevents any unwanted changes on your systems.
| The plugin brings a sizable number of directives (>100) and may obfuscate your current set of techniques and directives. Until it is better organized we strongly recommend to test the plugin in a dedicated test Rudder Server. |
The directives set is not meant to be used in Enforce mode without manual customization of the provided
configurations. Without any changes, it will most likely break your system.
Currently, the plugin is still in a Beta version and only support parts of the RedHat7 benchmarks. It is still in active development
and may not behave as you expect. Check the troubleshooting section below.
You can still try to make it works for other benchmarks, see below.
Prerequisites
This plugin needs the package rudder-api-client and python3-requests to be installed on your Rudder Server.
Usage
The plugin provides one rule per supported/builded benchmark to help you audit them with Rudder. We recommend to not modify the rules provided by the plugin and to apply them to your audit wanted groups of nodes. For most commons cases, skipping items on a per node basis as described below should be enough to adapt the rule set to your needs and will make eventual plugin upgrade much more easier.
Installation
As most of the Rudder plugins, you must install the plugin with the rudder-pkg tool on your Server Rudder.
/opt/rudder/bin/rudder-pkg install-file <path to the rpkg>
This will install a set of Techniques, Directives and Rules to your Rudder Server. All of them are tracked by the plugin and can be removed at any time by removing the plugin from the Server.
Uninstallation
When removing the plugin, you will be asked for each Rule/Directive/Technique if you want to remove it. Except if you did customize the Techniques or Directives distributed with the plugin, we strongly recommend to always wipe all the content distributed with it when asked for.
/opt/rudder/bin/rudder-pkg remove rudder-plugin-cis
Upgrade
Since the plugin provides a lot of different Rudder objects which you may want to modify, the upgrade process needs to be kept as simple as possible.
Currently, an upgrade is litteraly a remove followed by an install. It means that if you make changes on the provided configuration, you will need to skip the remove part of the modified directives and techniques if you do not want them to be replaced at upgrade.
How it works
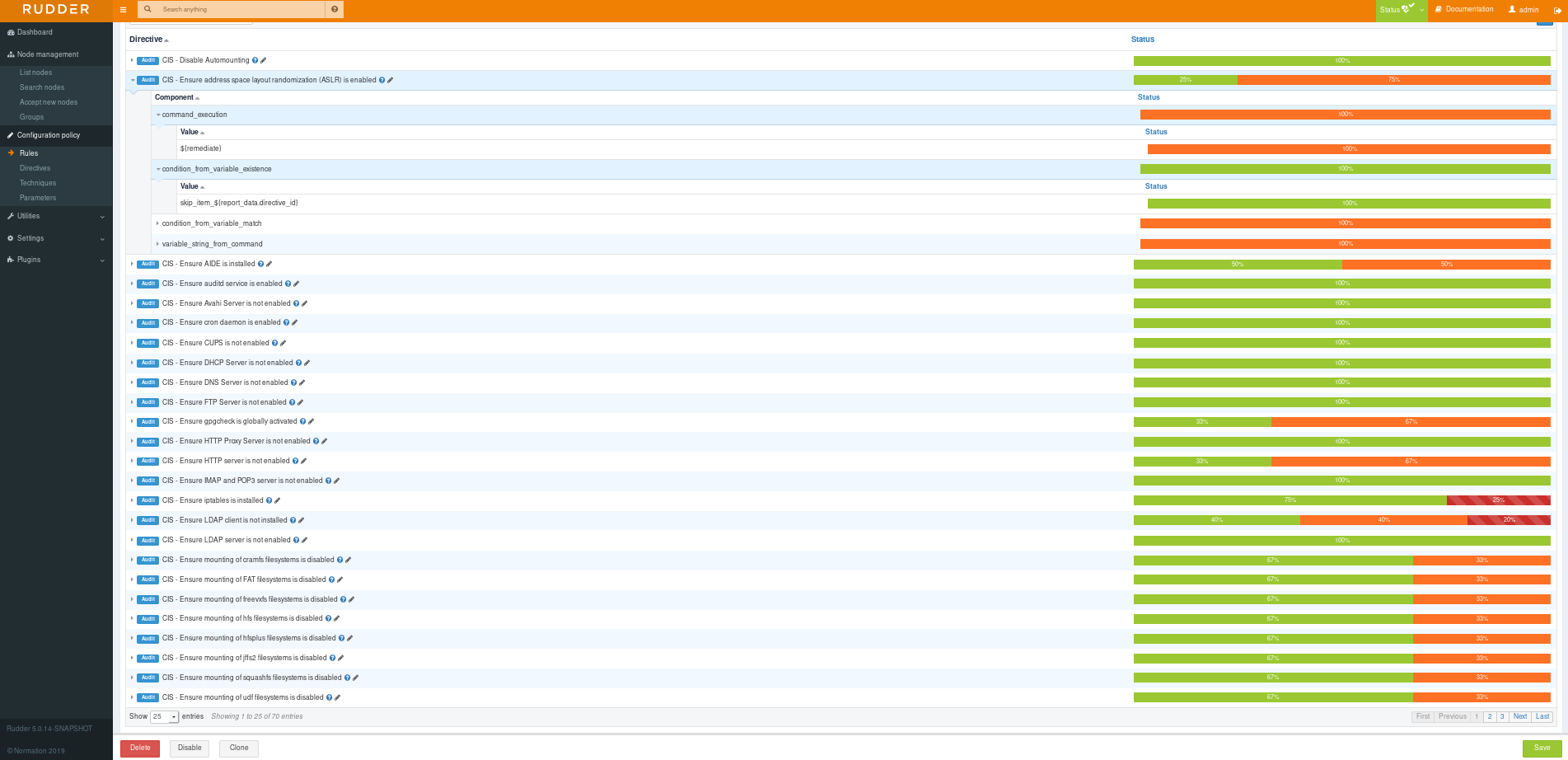
Each benchmark item will be translated as one or more directives with the following:
-
The
directive namefollows the syntax:CIS - <item name> (<extra infos if any>)-
Where
extra infosis optional and only used when a single benchmark item needs multiple directives to be audited. -
For the RHEL7 benchmark with the item: "3.2.4 Ensure suspicious packets are logged (Scored)" This items is declined in two directives, called: "CIS - Ensure suspicious packets are logged (net.ipv4.conf.all.log_martians)" and "CIS - Ensure suspicious packets are logged (net.ipv4.conf.default.log_martians)".
-
-
The directives are all tagged based on the benchmarks:
-
If we take one of the two directives descrive above we will have the following tags to help you organize and quickly search for specific items:
{ "cis-redhat7" : ["3", "3.2", "3.2.4"], #Based on the benchmark item number "cis-server" : "1", #Based on the benchmark level for server "cis-workstation" : "1" #Based on the benchmark level for workstation }
-
-
Each directive is based on techniques written from the
Technique Editor, this will let you modify it easily if needed.
Test a subset of the benchmark
In most cases you will not want to test every single items of the CIS benchmarks on your servers. You can skip items on a node basis without changing the rules provided.
To do it:
-
For a specific node, identify the CIS-directives that you want to be skipped and note their
Directive Rudder IDfound in their respective page undershow technical detailsin the directive tree. -
Add a JSON
node propertynamed skip on the target node containing keys corresponding to the previously notedDirectives Rudder ID.# An example of the skip property value to skip the "Ensure suspicious packets are logged" item { "0b8e988c-fa02-42a0-813c-e07ff6eafb9a": "True", "0b8e988c-fa02-42a0-813c-e07ff6eafb9a": "True" }
The skipping process is more detailed in the section below.
Troubleshootings
-
After install, the generation status in the Rudder UI may be in error, stating about some missing bundles, try to run a
rudder agent updateon your server, and force aPolicy Regenerationin the UI. -
Since the CIS plugin audits hundreds of components, you may come across some journald limitations, which may stop syslog before the end of the agent execution. This lead to non reporting nodes, and messages in /var/log/messages before the end of the agent execution like:
Oct 1 08:41:40 localhost systemd: Stopping System Logging Service...
This can be fixed by removing the burst limits in your journald configuration:
# In /etc/systemd/journald.conf RateLimitInterval=0 RateLimitBurst=0
Build for others benchmarks
The plugin build is based on pdfs benchmark parsing. Each items parsed from the pdfs will be tested by regex matching on their name with a directive bank put in the configuration folder.
If an item name matches with a directive name, it will tagg the directive based on the pdfs, edit its description and add it to the distributed configuration.
There is no proper check on what the directive is doing, we assume they were written by users and should be generic enough to support multiple benchmarks if the items name are identical.
To generate a plugin providing rules for one or more non supported benchmarks, deposit the associated pdfs in the pdfs folder with the folowing naming convention:
cis_<benchmark_short_name>.pdf
A modification in the Makefile (to remove the private download of the pdfs, made on our side) and in the "targets" variable defined in the tools/cis-tag will be necessary to build it at your convenience.
This will generate rules named: CIS - <benchmark_short_name> sample rule.
Each directives used in the different rules will then be tagged as follow:
# Ex with item 1.1.22 of the redhat7 benchmark cis-redhat7: 1, 1.1, 1.1.22 cis-server: 1 cis-workstation: 2
Extend, improve the directives
-
Install the plugin
-
Modify or create the directives or techniques you want to add to the plugin
-
Export them by running:
/var/rudder/packages/rudder-plugin-cis/rudder-synchronize export rule <rule-id> <destination-file>
-
And add the content of
<destination-file>/directivesand<destination-file>/rulesto the plugin repo under theconfigurationdirectory. -
You may need to run a build and a clean to normalize the newly added jsons.
Each added Technique should be as generic as possible to limit their number. Each one of them must start with a condition from variable existence defined as follows:
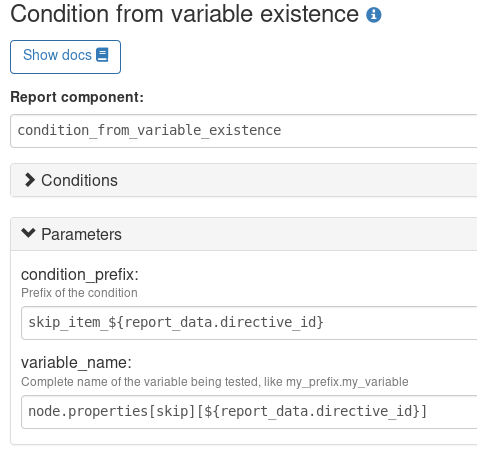
Each generic methods used in the Technique should then be guarded by the condition:
skip_item_${report_data.directive_id}_false
← Authentication backends Centreon →