Secret Management
The purpose of this plugin is to prevent exposing sensitive data at the interface level. A secret contains a:
-
name: the name will be exposed in the interface to refer to the value without exposing it. -
value: the value that we don’t want to expose in the interface. -
description: content to identify what contains the secret, it supports Markdown formatting. All these parameters are mandatory, they cannot be empty.
|
The value will not be displayed again in the interface after the creation, make sure to provide a precise description of the secret variable to be able to identify it. |
|
The value of the secret may still appear in agent logs, which are visible in the interface in:
|
|
The secrets are stored as clear text in the file located at |
How to use
-
Create a secret variable
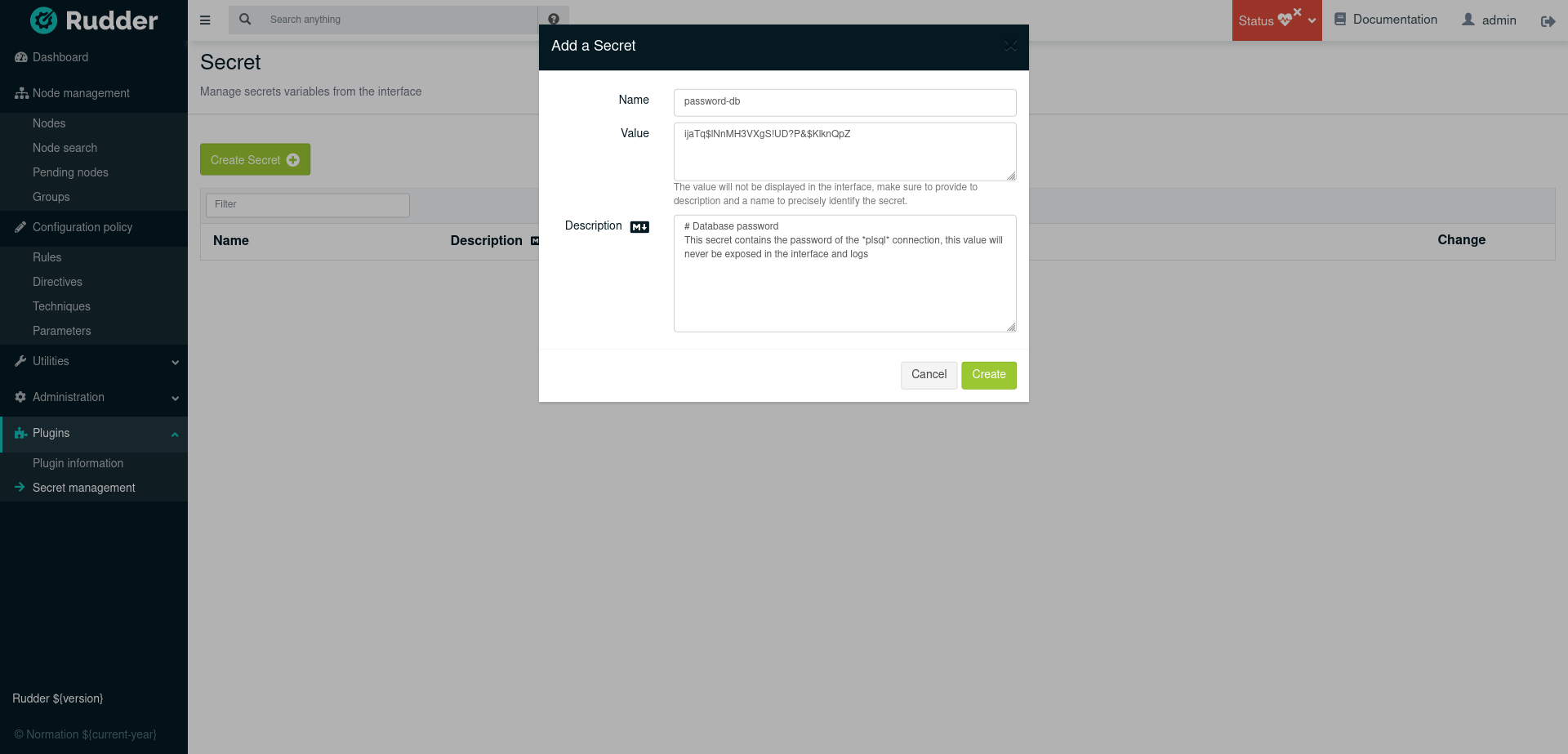
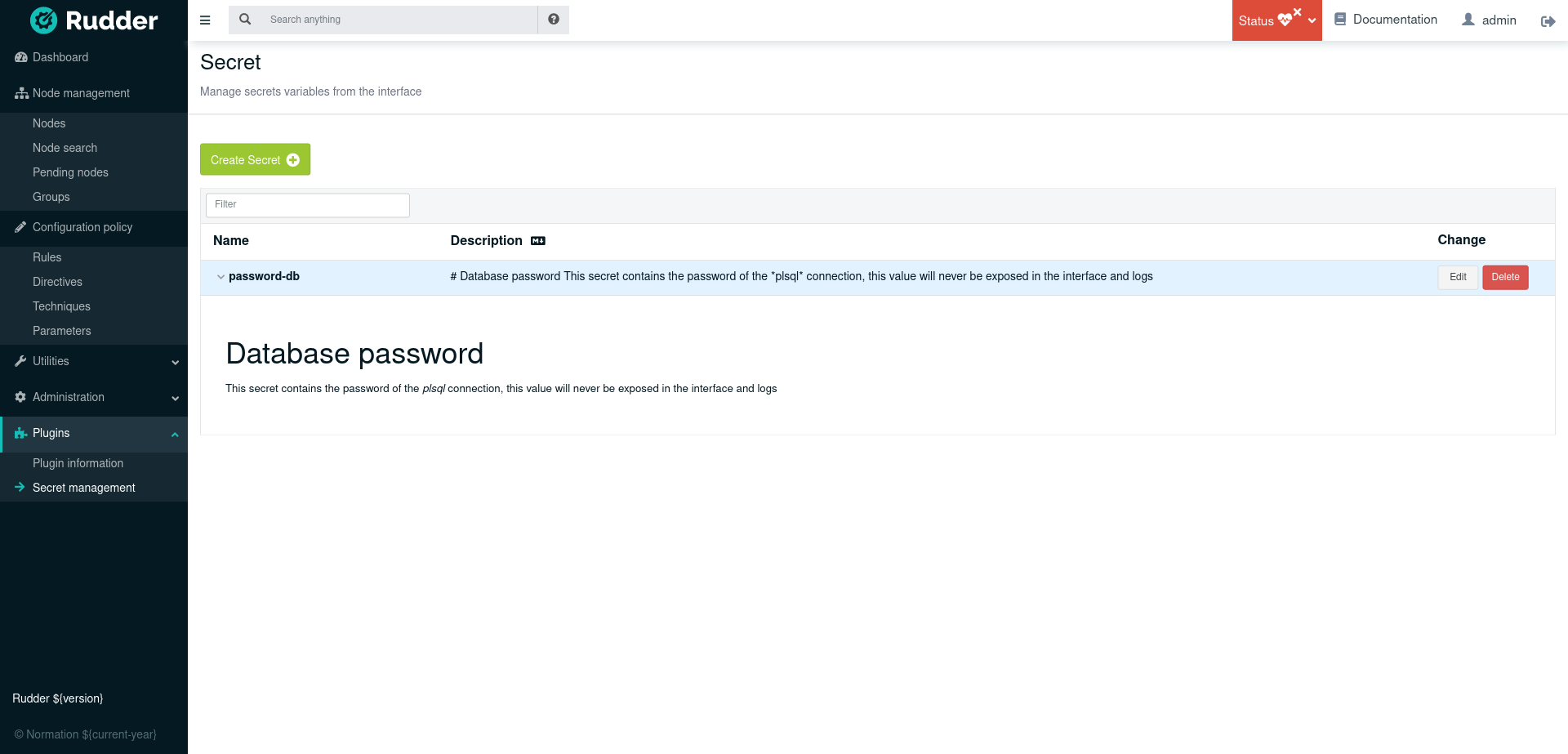
|
When a secret is edited, only non-empty fields are modified. |
|
Once a secret is created, you will not be able to modify its name from the interface. 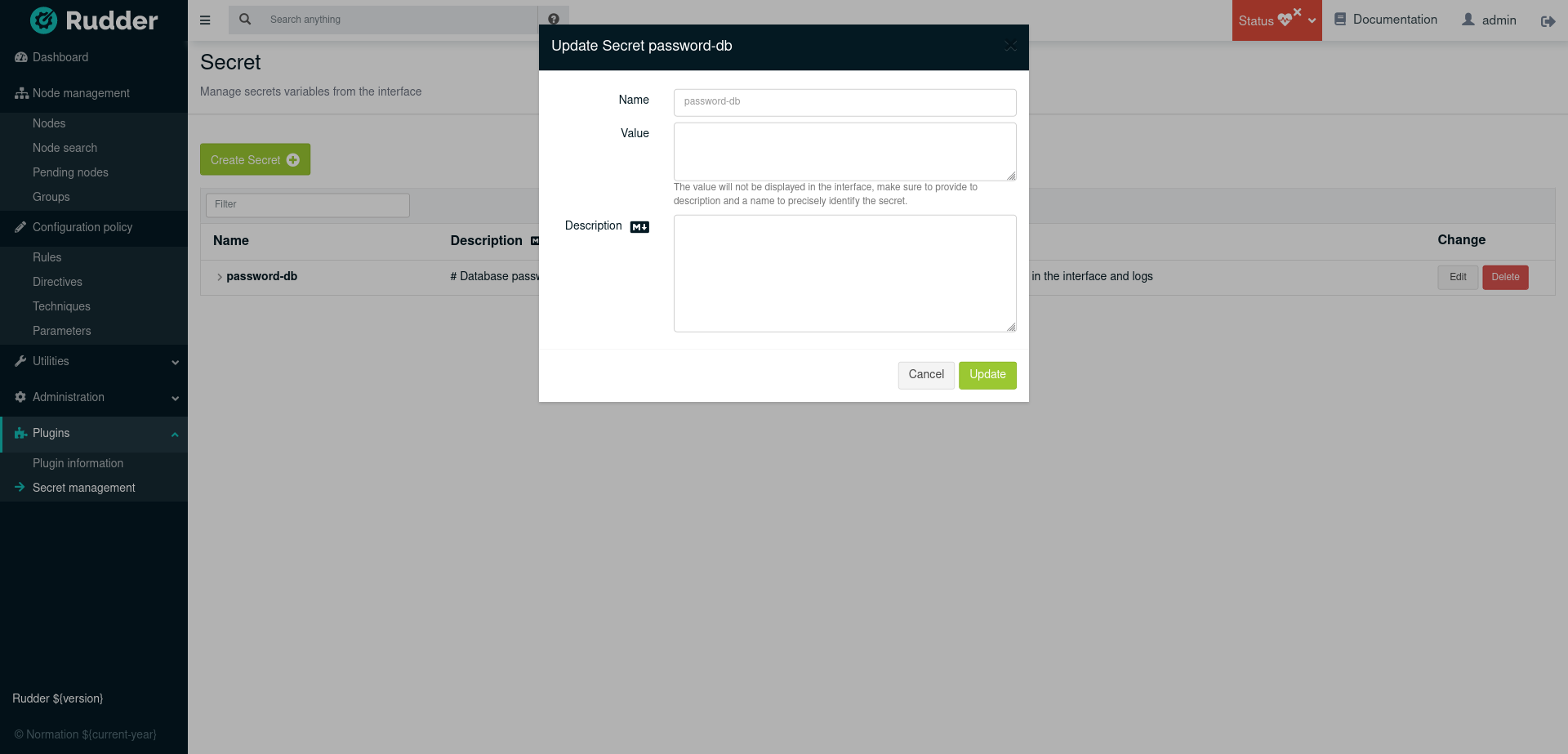

|
-
In a node property use the format
${data.secret[secret_name]}or${rudder-data.secret[secret_name]}in a JSON
|
Secrets can be used in directives and properties. However, they cannot be used directly in the Technique Editor; if you need to use your secrets inside a technique, you’ll need to add a technique parameter and set the secret in the associated directive. |
-
The value will be interpolated by the real value of
secret_namecreate earlier in the plugin interface
← Scale out relay servers System updates →